Security Concept
Maximum security
for your production data
manubes Security Assurance
Our Security Concept
With constant technological progress being made in areas such as industrial connectivity and automation, an important focus has to be placed on the security and reliability of the industrial data exchange.
With manubes, your production data is protected from any unauthorized access. At the same time, various mechanisms ensure that the system is fail-safe.
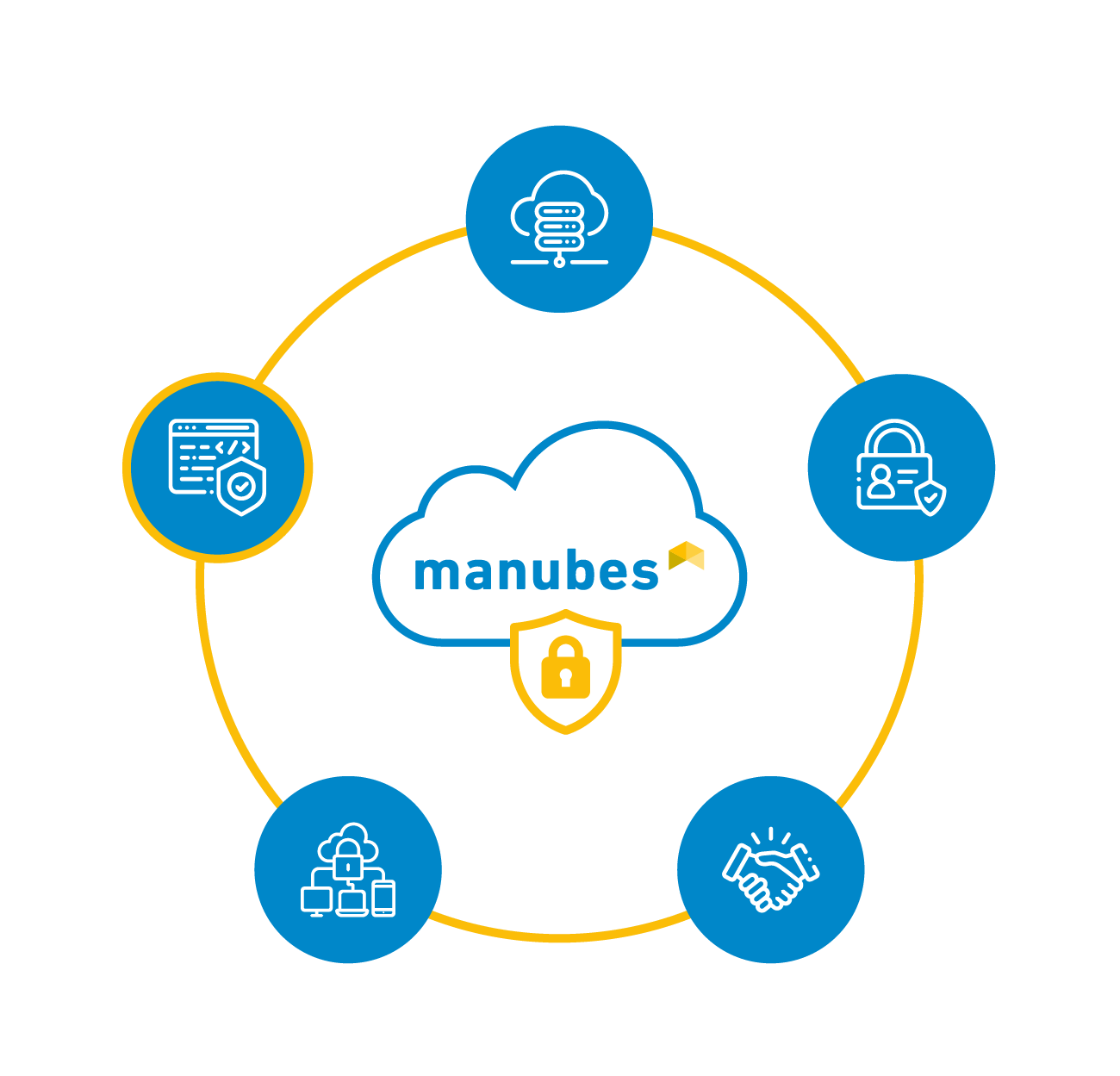
The 5 pillars of manubes security
The manubes security concept is based on the following five pillars which will be explained in more detail below.
manubes Secure Infrastructure
Secure Cloud Infrastructure
Secure cloud environment:
manubes is based on the Microsoft Azure infrastructure, one of the most widely used cloud computing environments. Azure offers a wide variety of security mechanisms which we integrate into manubes.
End-to-end-encryption via SSL/TLS:
All data transfers between the manubes servers and our customers are encrypted with state-of-the-art technology and cannot be accessed by any third party.
No access to customer resources (Zero Trust):
manubes gives our customers full control over their data. The platform was developed in a way that ensures we have no access to customer resources. Only employees who have been explicitly authorized by the customer can access such data.
manubes Access Control
Access Control
Extensive authorization concept:
manubes implements an extensive authorization concept that protects data, workflows and other areas of the system from unauthorized or unintentional access. Individual users or user groups are only granted access to the data and actions intended for them.
Login security:
By using Microsoft as an external login provider, manubes prevents the risk of phishing attacks. In addition, login security is enhanced by further mechanisms such as 2-factor authentication. User credentials are stored in a secure and encrypted database that can only be accessed by authorized services.
manubes Reliability
Stability & Reliability
Fail safety:
The manubes platform is designed to be available anytime and anywhere. It is based on a stateless architecture with a redundant design that avoids failures. It also uses Edge Clusters technology to ensure a reliable connection to its local data sources, even if individual components are disrupted.
Performance optimization:
The manubes platform dynamically adapts to the requirements of its users. If more requests are made to the platform, it automatically increases the available resources without interrupting the running processes (horizontal scaling). This ensures high performance. manubes also uses load balancing to optimize the utilization of the platform. This applies to both the cloud and the Edge Clusters that are operated on-premise.
manubes Operational Safety
Secure Integration
Protection against unintentional modifications:
By implementing versioning, edit traceability as well as extensive backup and data recovery functionalities, application development with manubes provides maximum protection against unintentional changes. In addition, the use of test environments on the customer side ensures that live operations are not affected during application development.
Data recovery:
By default, data deleted by users is not immediately removed completely from the database, but only marked as deleted. This way, accidentally deleted data can be recovered if necessary.
manubes Secure Development
Secure Software Development
With more than 25 years of experience in industrial software development, we at inray implement a wide variety of security standards in our programming. The following list contains only a few examples:
- 5Blue-green deployment
- 5Four-eyes principle
- 5Git version control
- 5TraceID error tracking
- 5Monitored code guidelines
The manubes platform is under constant development in compliance with the highest standards of security, quality and integrity.
Read the Complete Security Concept
We will be happy to provide you with the full manubes security concept in PDF format via e-mail. If you have any questions, you can reach us through our contact form at any time.
